Setting up an Identity Provider for Snap XMP Online
This document details how to set up Microsoft Azure AD and OKTA as Identity providers for Snap XMP Online.
Setting up Microsoft Azure AD/Entra ID
Register a new Enterprise Application
Click “New registration” under Enterprise Applications.
Set up Single Sign On
By default, Microsoft does not seem to give access to SAML functionality. One way to get this working is to select the “Microsoft Entra SAML Toolkit” from the gallery and customise. To find it, search for “entra saml”

Select the entry “Microsoft Entra SAML Toolkit”. In the popup window, change the name and logo, and click “Create”.
Go to the Single sign-on section of the application:
Select “SAML”.
Enter the required information. shows online1.snapsurveys.com as an example:
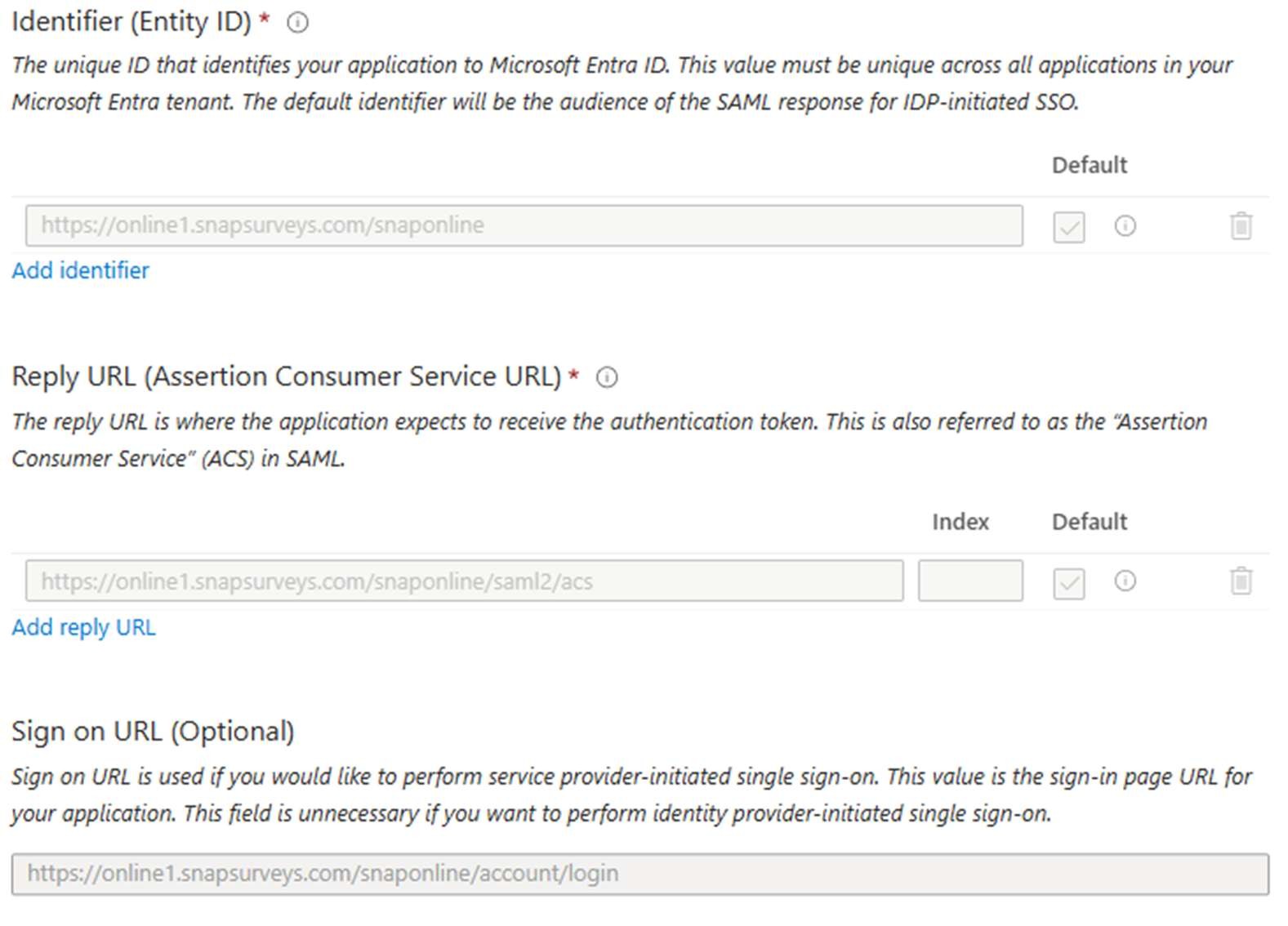
When finished, the first configuration section should look like this (allowing for URL):
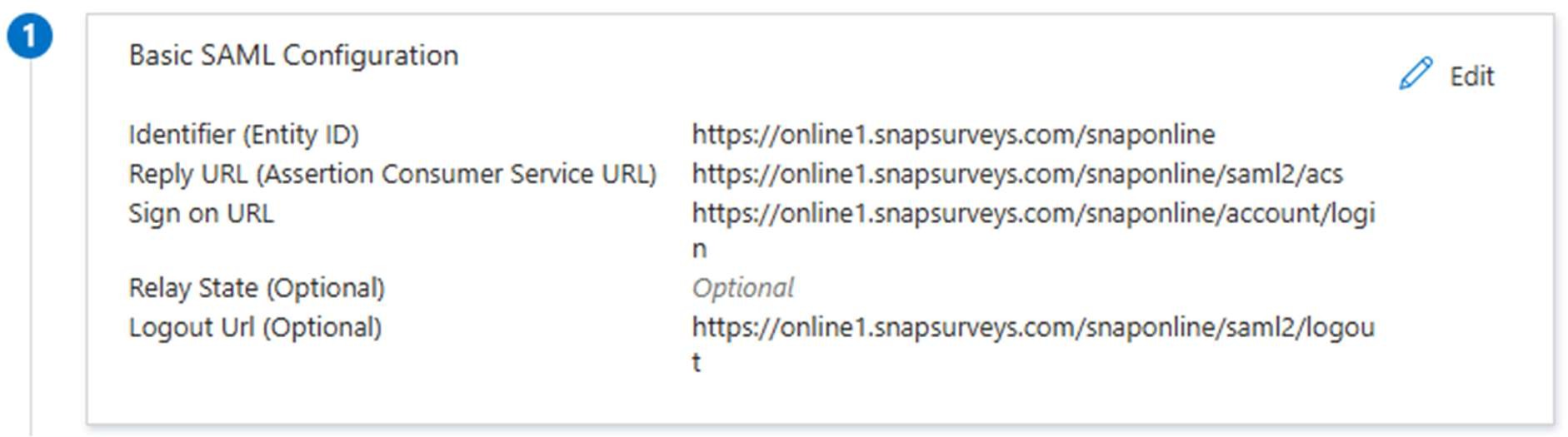
NB: We do not use the Relay State so this does not need to be filled in.
Add the “username” Claim
Click edit in the “Attributes and Claims” section and add the username claim, pointing to the user.mail address. This tells Snap XMP Online how to find the correct user details for log in.
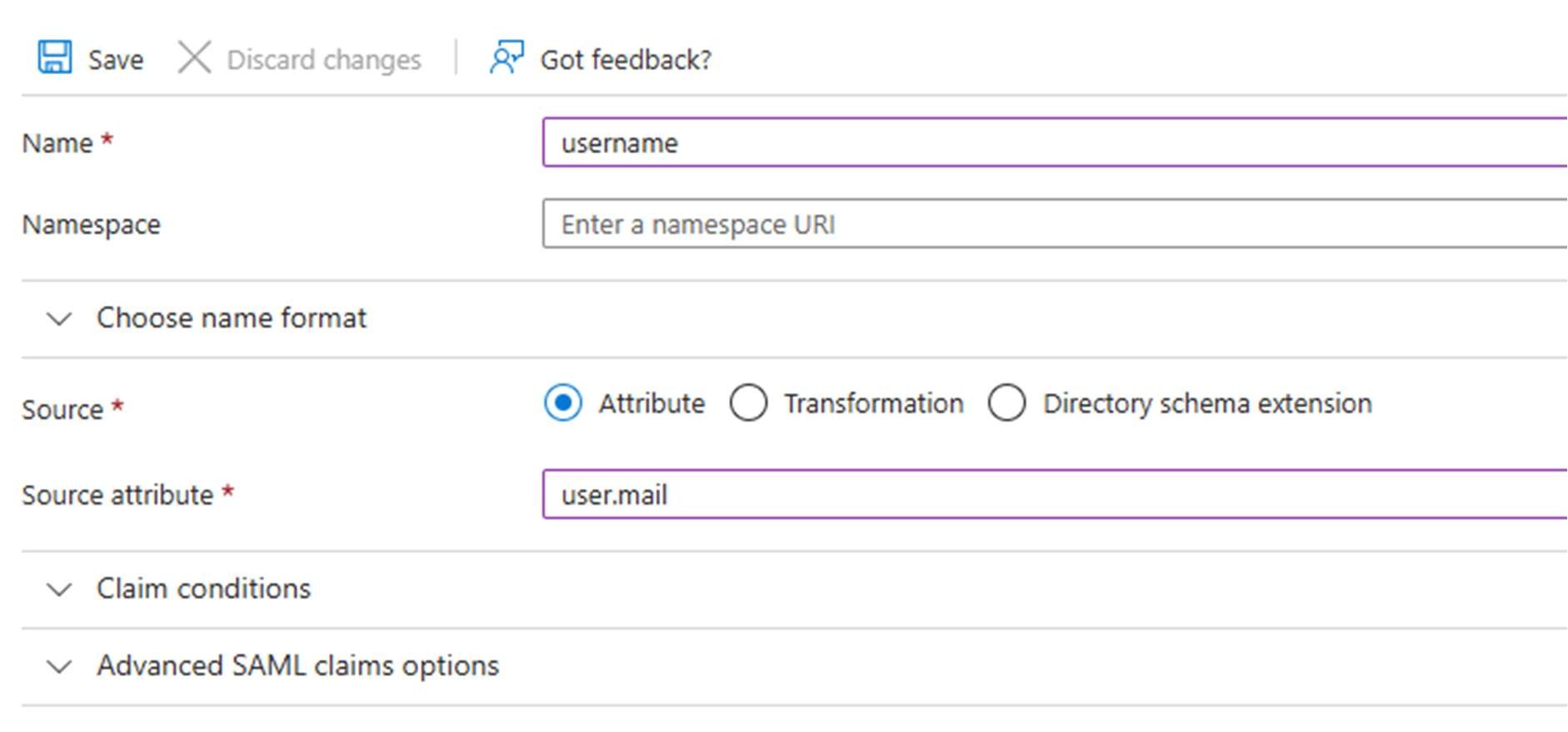
When finished, the second section should look like this:
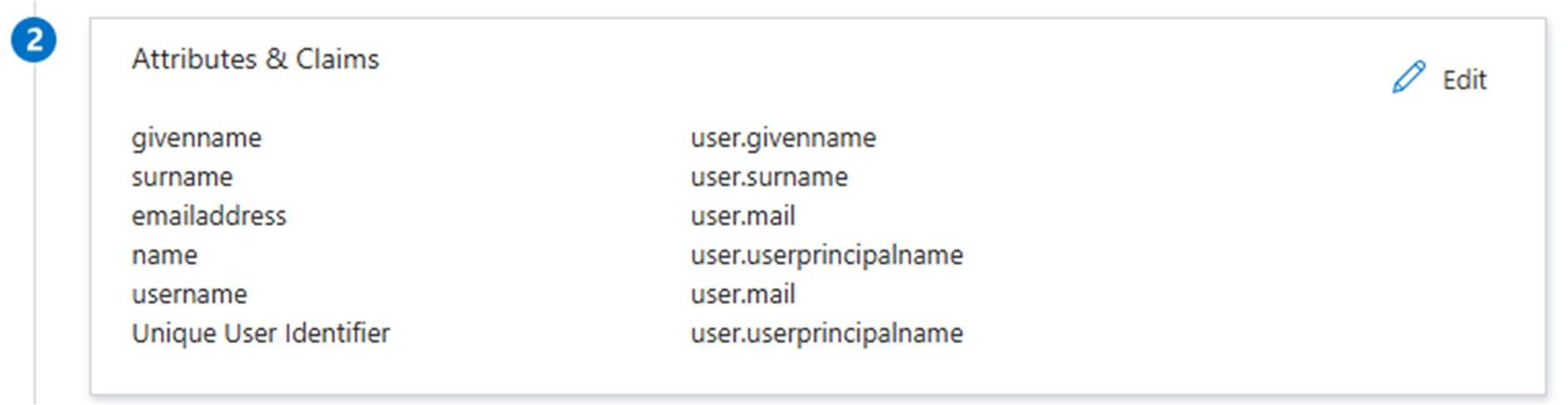
Provide values for configuration in Snap XMP Online:
From the third and fourth sections, we need to add the following information:
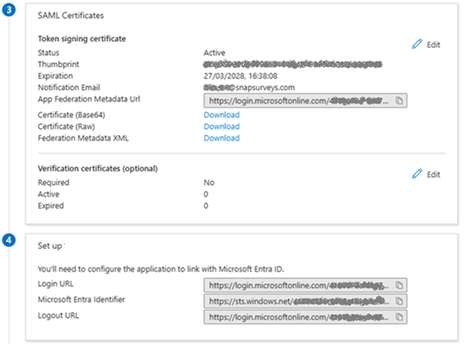
- App Federation Metadata Url
- Login URL
- Microsoft Entra Identifier
- Logout URL
Setting up OKTA
Log in as Admin – you can find this option in the top-right of the OKTA interface, by your username. You should get to this admin screen:
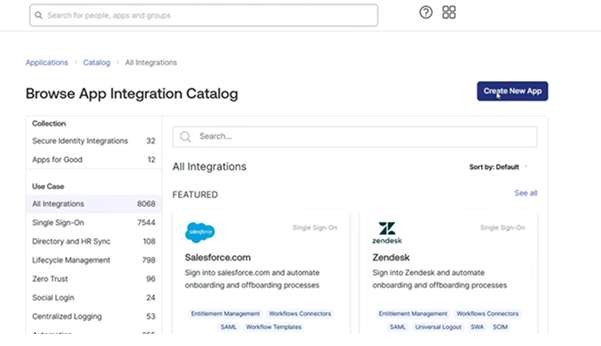
Select “Create New App”. You should see a pop-up dialog:
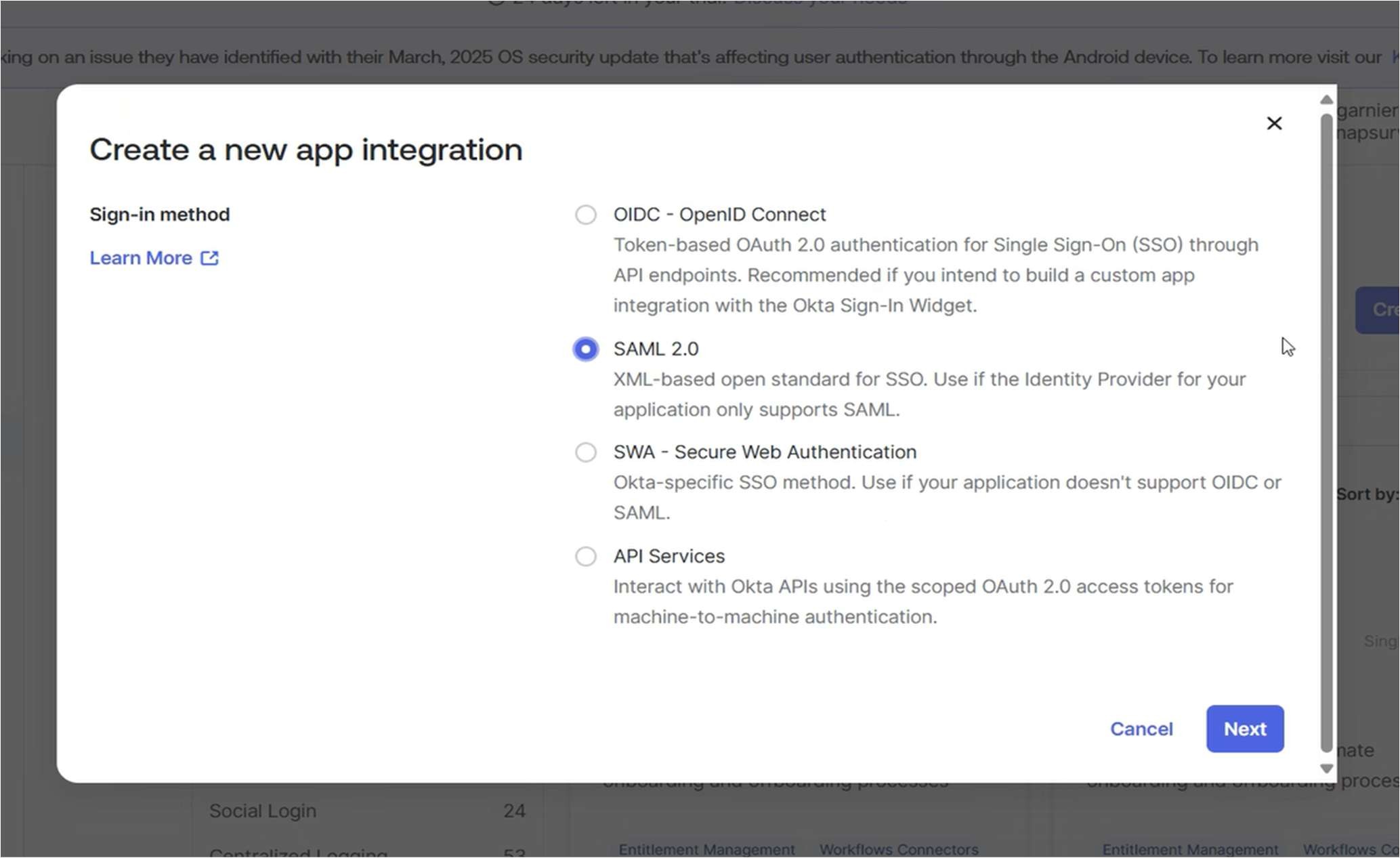
Select SAML 2.0 and press “Next”.
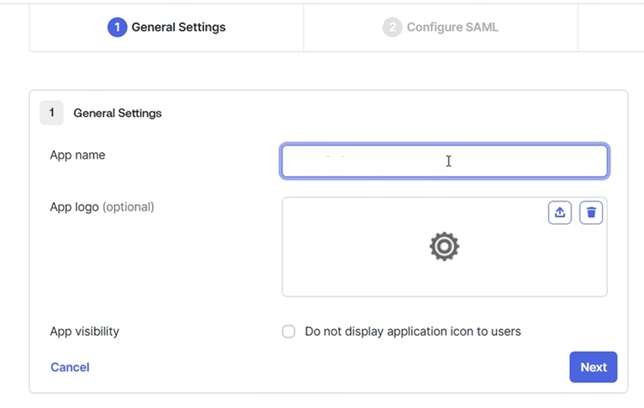
Give the new app a name and click “Next”.
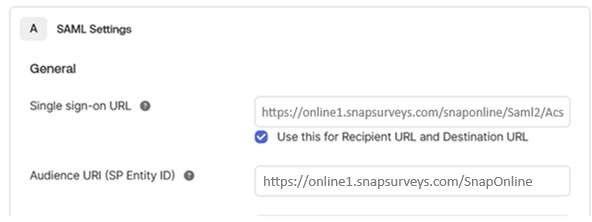
The Single Sign-On URL needs to be set to: https://online1.snapsurvey.com/SnapOnline/Saml2/Acs. The SP Entity ID needs to be set to: https://online1.snapsurveys.com/SnapOnline.
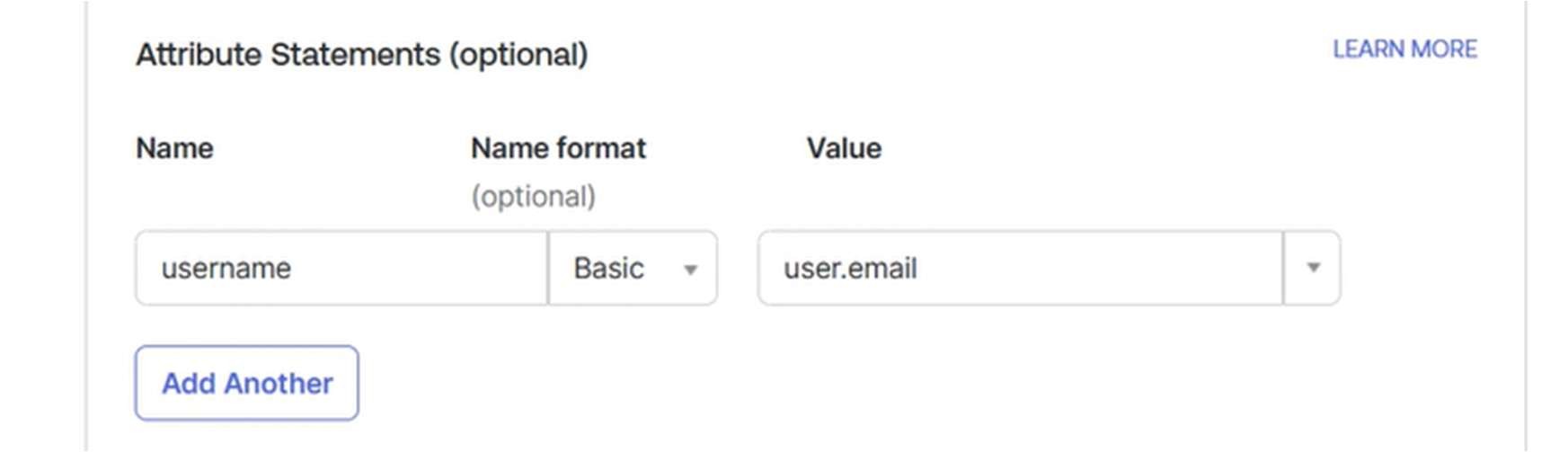
Add an attribute statement with the Name “username” and the value “user.email”. This is to allow Snap XMP Online to match the OKTA user to a Snap XMP Online user.
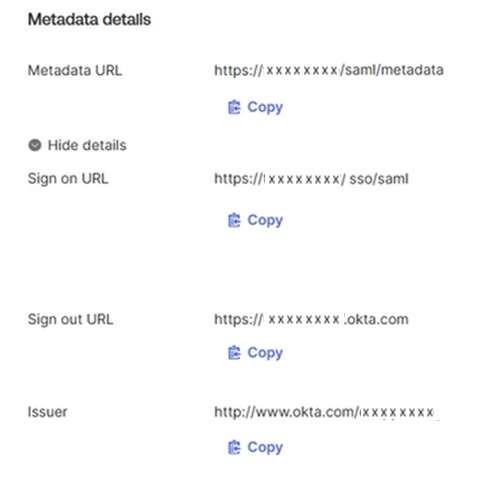
The next screen contains the information needed for Snap XMP Online:
- Metadata URL
- Sign on URL
- Sign out URL
- Issuer